SQL injection: Process, Prevention with example
SQL injection is a type of security vulnerability that occurs when an attacker inserts malicious SQL code into a query, ...
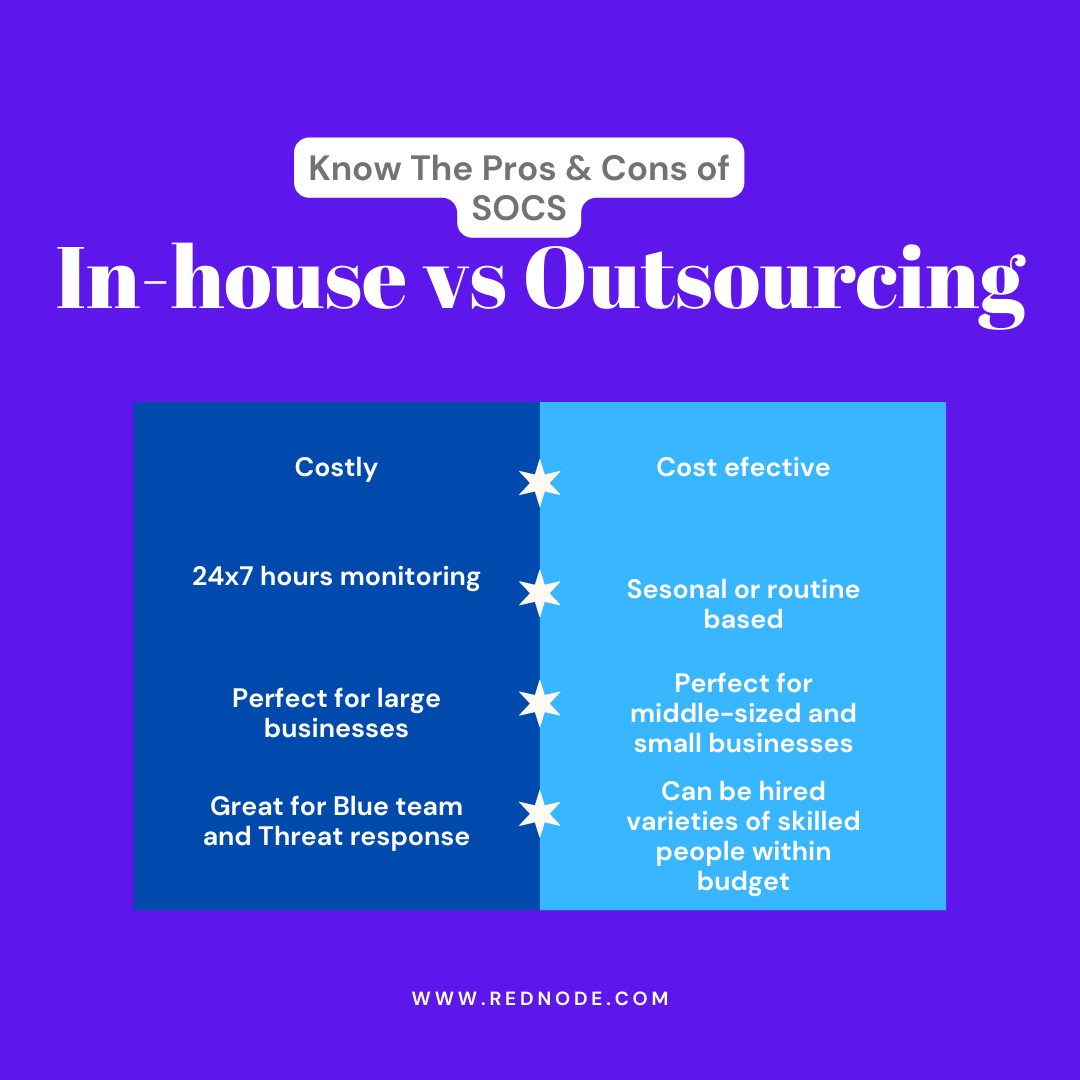
Outsourced SOC vs In house SOC: pros, cons, and differences
SOC stands for Security Operations Center. The term cyber security operations are directly related to modern business. They need cyber ...

Red Team vs Blue Team: Understanding as a Service
Red team refers to a group of authorized and organized people to emulate a potential cyber attack on a modern ...

Personal cyber security tips to improve personal cyber security
Personal cyber security refers to an individual’s security in the cyber world. Personal protection protects a person from cyber threats. ...

Best practices to secure network: Prerequisite Knowledge (part 1)
In this world, everything is connected with networks. In the digital world, every device is connected through networks. If our ...

Best practices to secure network: Practices (part 2)
This is the second part of securing networks. Here we will describe practices to secure networks. The first part is ...

Antivirus: Good Sides and Bad Sides
Antivirus is an important tool for every person who uses computer devices. Antivirus has good uses and has some bad ...
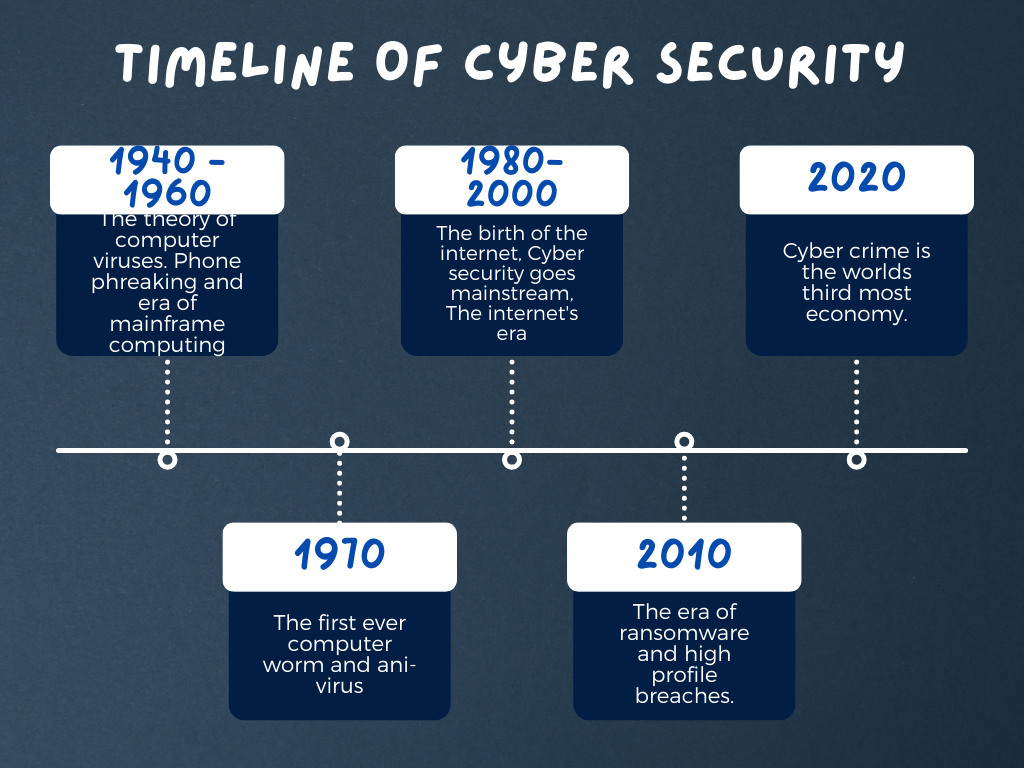
Timeline of Cyber Security: The Fascinating Evolution
the timeline of cyber security began in 1945 with the invention of the modern computer named ENIAC. But the term ...

Ethical Hacking vs Penetration Testing
The model of cyber security is very much complex. In the upcoming days, the model will become more complex. It’s ...

Penetration Testing vs Vulnerability Assessment: Top 6 bold differences
Penetration testing and vulnerability assessment both are essential for an organization’s cyber security. But most organizations or individuals can’t decide ...
API Security Testing Checklist: 5 steps to secure your API
What is the API security testing checklist? API Security Testing Checklist means a structured list that outlines specific steps to ...

