importance
Why is Web Application Penetration Testing?
Easy access for cybercriminals
Any front-facing service is a common target for cybercriminals. Web Application is one of the critical services that cyber threats target for easy initial access. Never leave it unprotected.
highly Reward for Cyber threats
Web application vulnerabilities can be exploited easily with low detection, but it is still highly rewarding for them. A vulnerable web application could lead the attacker to compromise the entire infrastructure.
Vital To Protect Your Business
A successful attack against your web application may lead to compromising your customers and sensitive information, which has a massive impact on any business. Never leave the web application unchecked.
Let Us Protect Your Business

What is Web Application Penetration Testing
Web application penetration testing is a process of real-world simulated attacks on websites to detect web application flaws that can be exploited by threat actors. Web pentesting is similar to network penetration testing but this testing only focuses on web applications.
RedNode’s penetration testers are OSCP, OSWE, OSEP, OSED, and OSCE3 certified. Our elite team can help you to identify security flaws in your web application and remediate them.
Key Benefits of Regular Pentesting
A threat actor may be trying to find flaws in your web application to breach your network or other sensitive data. Web Application Penetration Testing is the best way to identify the vulnerabilities before the threat actors.
By doing penetration testing, you can determine the current complete security posture of your organization. You can address every possible weakness and improve the overall security posture.
If your website has personal information, do transactions, and hackers may disrupt your business. Also, No one usually feels safe, if there is any breach. Strong security is always a green signal for your customers. And pentest your web application is the best way to make sure about web app security.
By performing regular web application penetration testing, you can detect existing vulnerabilities and other security weaknesses. If the vulnerabilities and weaknesses are not remediated before getting exploited by attackers, a data breach may happen. You can identify the recent vulnerabilities and weaknesses and reduce the attack surface.
If you leave weakness alone, anytime it can be exploited by cyber threats. And Data breaches or network downtime may occur. Recovering from such an incident is very expensive. You can prevent this costly incident by performing regular penetration testing by certified and experienced security experts.

Web Penetration Testing Methodologies
We have five penetration testing phases that help to assess your security posture. Every step are carefully followed to ensure the best possible result at the end.
1. Planning & Preparation
Before performing web application penetration testing, we identify critical domains and subdomains and define the testing goals and scopes. Then, create a detailed plan around the conduction of the engagement.
2. Reconnaissance
We perform information gathering and enumeration to find attack vectors in your web application, both with automation and in-depth analysis. During the recon phase, we gather information about your infrastructures, servers, domains, subdomains, IPs, etc.
3. Vulnerability Assessment
We combine our manual test with highly sophisticated open sources and commercial tools to identify vulnerabilities in your web applications.
4. Exploitation
Once stage 3 is completed, RedNode’s penetration testers attempt to exploit the identified vulnerabilities safely. Here, we validate the vulnerabilities and eliminate the false positives.
5. Reporting & Retesting
RedNode Penetration Testers document the findings and create Proof of Concept. Then provide a vast and detailed report at the completion of the assessment with remediation procedures.
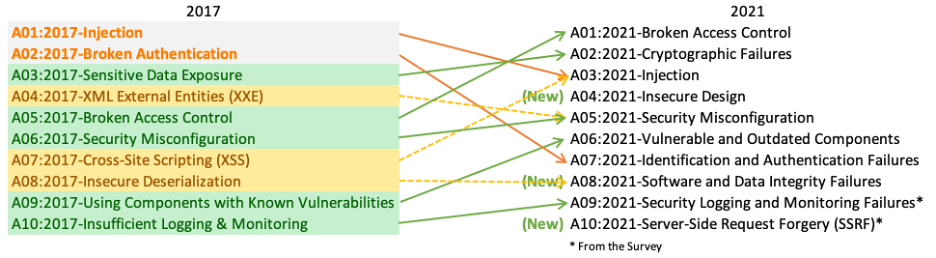
Web Application Vulnerabilities
Our web application testing is based on OWASP TOP 10, 2021. Our Expert penetration testers test for all possible web vulnerabilities to make sure you are 100% safe.
Authentications Flaws
Even if the sensitive resources are password, a skilled attacker may be able to break it. So we make sure, we test for all authentication vulnerabilities Such as Default Credentials, Lockout policy, Authentication Bypassing, Weak security Testing or password reset vulnerabilities, multi-factor authentication, and many more.
Our highly skilled professional penetration testers will make sure no authentication flaws is missed to check.
Authorization and Session flaws
What if an attacker login(or without login) as a normal user but also can access the administrator resource? It is very important to test various authorization and session vulnerabilities.
By web application penetration testing, we check for all possible authorization vulnerabilities such as Directory Traversal, Direct Object Reference, CSRF, Session Hijacking, and many others.
Input validation
If your web applications accept user input, The web application may get compromised, and if it is not sanitized correctly. Wrong input validation is the most dangerous weakness for a web application.
The input validation testing must be performed by a well-experienced and certified penetration tester. Redtm’s Penetration tester will make sure to test all possible input validation vulnerabilities such as Sql Injection, Remote command injection, XML injection, Template injection, Objection injection, and many more.
Client Side Vulnerabilities
Even if the client-side vulnerabilities are not dangerous as the server-side vulnerabilities, these vulnerabilities are still considered high-risk vulnerabilities. Because using these client-side weaknesses, an attacker can steal sensitive information, install malware, and can perform phishing attacks.
Vulnerabilities like Cross-site scripting, ClickJacking, HTML injection, Open Redirection, or Cross-Origin Resource Sharing should never be left unfixed. We will test for all client-side vulnerabilities listed in OWASP.
