Template injection vulnerability occurs when attackers can inject malicious templates into the applications. Templates are used in applications to make them dynamic. Also, templates are used to combine dynamic and static data to make the final output. When an application fails to sanitize or validate user input that is used within templates, it can lead to template injection vulnerabilities.
Modern web applications are highly dependent on templates that’s why most web applications are vulnerable to template injection vulnerability. Template injection vulnerability forces applications to execute malicious commands or leak sensitive data.
A vulnerable code snippet might look like this (Python Flask example):
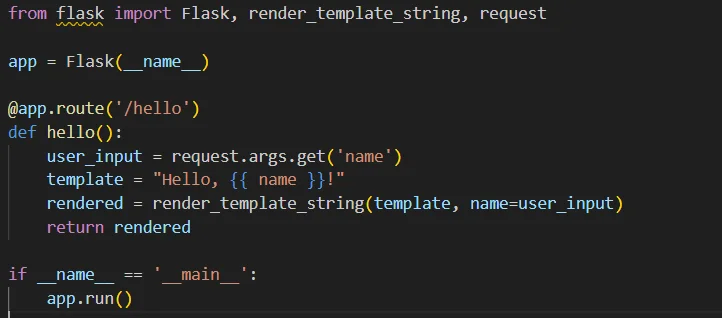
In this example, if an attacker provides {{ 7 * 7 }} as the name parameter, it will be executed as template code and the output will be “Hello, 49!”.
To fix template injection vulnerabilities:
- Sanitize Input: Always validate and sanitize user input before using it in templates. Input should be treated as data, not code. Bad sanitization will treat input as a code, a developer must be aware of that.
- Contextual Escaping: Implement proper escaping mechanisms based on the context in which the data is being used. This prevents any user input from being treated as executable code.
Here’s a fixed version of the above code snippet:
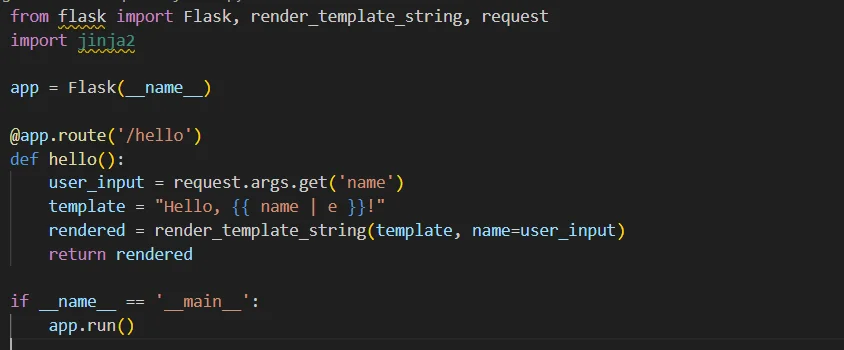
In this fixed version, the | e filter uses Jinja2’s built-in escaping mechanism to prevent any malicious code injection.
As for exploits, the impact of template injection can vary. Exploits can range from simple data leakage to full server compromise depending on the context and capabilities of the template engine being exploited. Exploits can involve executing arbitrary code, accessing sensitive data, and more.
Note that specific exploits can vary widely based on the template engine and application context, and it’s essential to stay updated on the latest security practices to defend against these vulnerabilities.
Another Example Of Template Injection Vulnerability (with exploits)
Here’s an example of a template injection vulnerability in a hypothetical web application using Python Flask and Jinja2 template engine:
Vulnerable Code
Suppose you have a web application that displays user comments on a blog post:
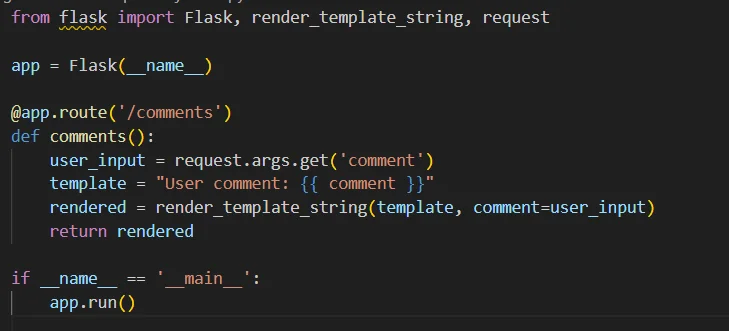
In this example, the user’s comment is directly embedded into the template without proper escaping or validation.
Exploit
An attacker could exploit this vulnerability by injecting malicious template code in the comment input. For instance, they might enter the following comment:
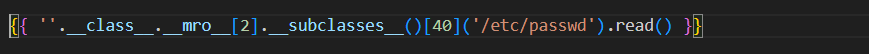
This code accesses the mro (method resolution order) the attribute of an empty string object to access the list of classes in the Python runtime then retrieves the 41st class in the list (assuming it’s the subprocess.Popen class) and uses it to read the contents of the /etc/passwd file.
When this comment is displayed on the blog post, the malicious code will execute, and the contents of the /etc/passwd The file will be leaked.
Fix
To fix it, a developer should sanitize and escape the user input before adding it to the template. Here’s how a developer can fix the code:
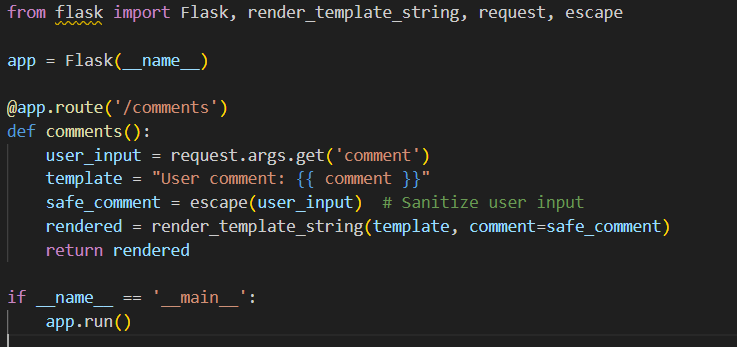
In this version, the code sanitizes and escapes each user input before adding to the template.
Remember that the specific payloads and exploits can vary based on the template engine and application context. It’s crucial to follow best practices for input validation and escaping to prevent such vulnerabilities in your applications.
Contact RedNode to secure your Application.

