SQL injection vulnerability refers to a type of vulnerability where the application fails to sanitize user input accepts malicious SQL commands as input and executes them on the backend server. SQL injection vulnerability is one of the high-severity vulnerabilities. SQL injection vulnerability can cause major damage to an organization.
Table of Contents
Example Scenario
Let’s think about an example scenario where you are testing a web application’s login form. The login form code might look like below:
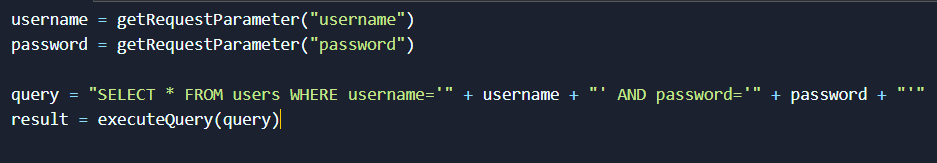
In this scenario, the web application takes user input without proper sanitization and directly uses it for their SQL query. The application is vulnerable to SQL injection vulnerability.
Exploiting SQL Injection Vulnerability
An attacker might try to manipulate the login process by inputting malicious data. Let’s say the attacker enters the following in the username field:
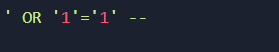
The modified query would look like this:
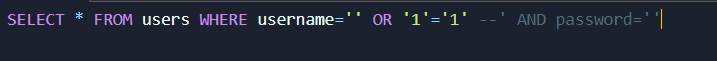
The -- symbol denotes a comment in SQL, effectively commenting out the rest of the query. The injected code '1'='1' always evaluates to true, effectively bypassing the password check and allowing the attacker to log in without a valid password.
Impact of Successful Attack
If the attack is successful, the application might grant the attacker unauthorized access, potentially exposing sensitive user data, administrative privileges, or even the entire database.
Are you Safe?
Stay safe from SQL Injection
Mitigation
To prevent SQL injection, developers should use parameterized queries or prepared statements, which separate user input from SQL code. Here’s how the example code should be secured:
Vulnerable Code (without protection)
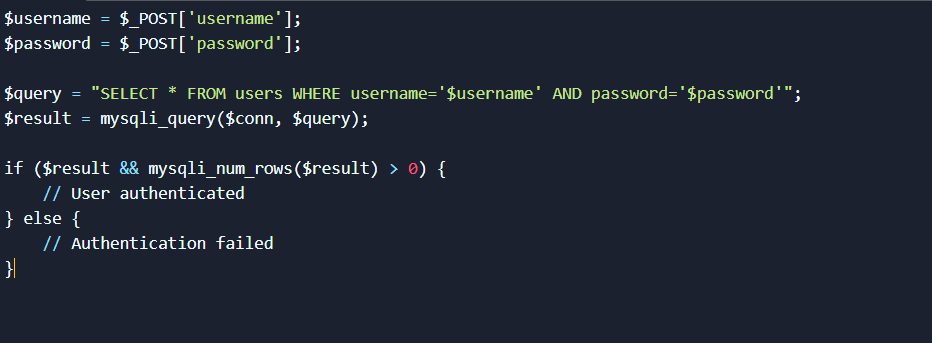
Fixed Code (with parameterized query)
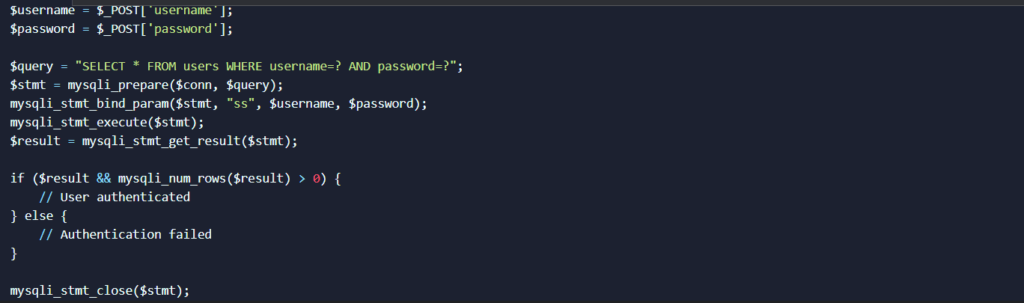
In the fixed code, the parameters (username and password) are bound to placeholders using mysqli_stmt_bind_param(), and the query is executed using a prepared statement. This prevents the user input from being directly interpolated into the query, effectively mitigating the SQL injection risk.
Using parameterized queries ensures that user inputs are treated as data and not as executable SQL code, making it much harder for attackers to inject malicious code.
Remember, the examples provided are simplified to illustrate the concept. The real-world scenarios are much more complex and harder to find and exploit SQL injection vulnerability.
Contact RedNode to save your application from SQL injection.

